Installation File/木马安装程序是exe文件:
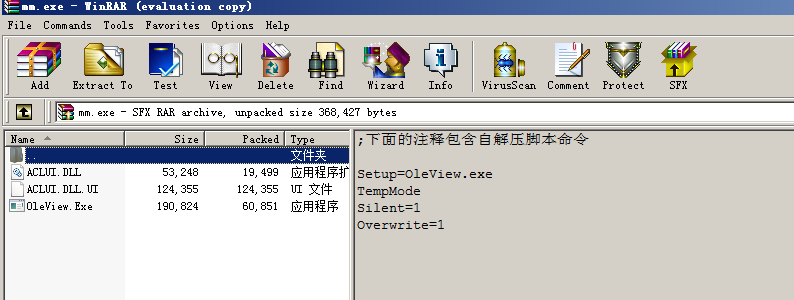
 winrar self-extracting exe file with few parameter to make it less noticeable.
winrar self-extracting exe file with few parameter to make it less noticeable.
Installation path/我的这个安装路径:
C:\ProgramData\OleView
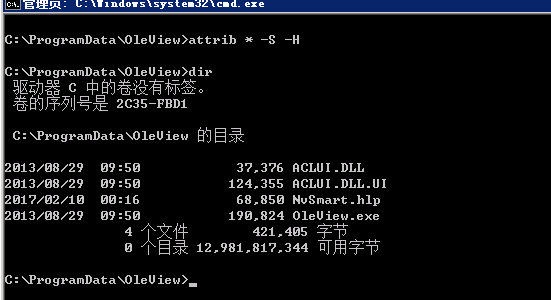
use attrib command to remove the system and hide property.
3个文件本身有系统隐藏属性 用文件夹选项的显示隐藏文件是选项是不能被查看到的
通过attrib命令去掉系统S和隐藏H属性就可以查看了。
OleView.exe is a win exe with complete valid digital certificate. anti-virus program won't check it loading resource like dll when exe have a good digital certificate signature.
OleView.exe是正常的window程序有完整的数字签名.杀毒软件会忽略它加载的dll之类的东西。
ACLUI.DLL is hard encode inside the OleView.exe. When OleView.exe run it will load ACLUI.DLL which is modified by hackers.
ACLUI.DLL是硬编码在OleView.exe中的dll。exe文件运行就会加载ACLUI.DLL。这个dll就是被黑客修改过的。
ACLUI.DLL will load ACLUI.DLL.UI after itself been loaded. and ACLUI.DLL.UI is a so called payload object file which is an encrypted hacker codes. Because it an encrypted hacker code object file. The file itself won't be reported by any anti-virus program. When loading the payload.the program raise anther 2 process svchost and msiexec and release/inject the virus code into svchost and msiexec. Run a antivirus program to check the memory will report svchost and msiexec have problem, but it's only when they are in memory. static files are fine file.
OleView.exe 加载ACLUI.DLL。ACLUI.DLL加载ACLUI.DLL.UI。并在这个过程中释放工作代码,开启svchost和msiexec。把木马工作代码注入到svchost msiexec。Oleview自己结束自己的进程。Svchost和msiexec驻留系统内存。硬盘上的svchost 和msiexec是正常文件。只有系统内存中被注入木马代码的这两个文件才会被杀毒软件报毒。
some NvSmart.hlp file are key-recorder files.
相同文件夹下会出现NvSmart.hlp文件这个文件用文本编辑器打开是 记录了 服务器使用者打开的程序和网站饼记录进行的 键盘操作。
according to refer ,build a decryption tool.
根据这里的说明,做解密工具。
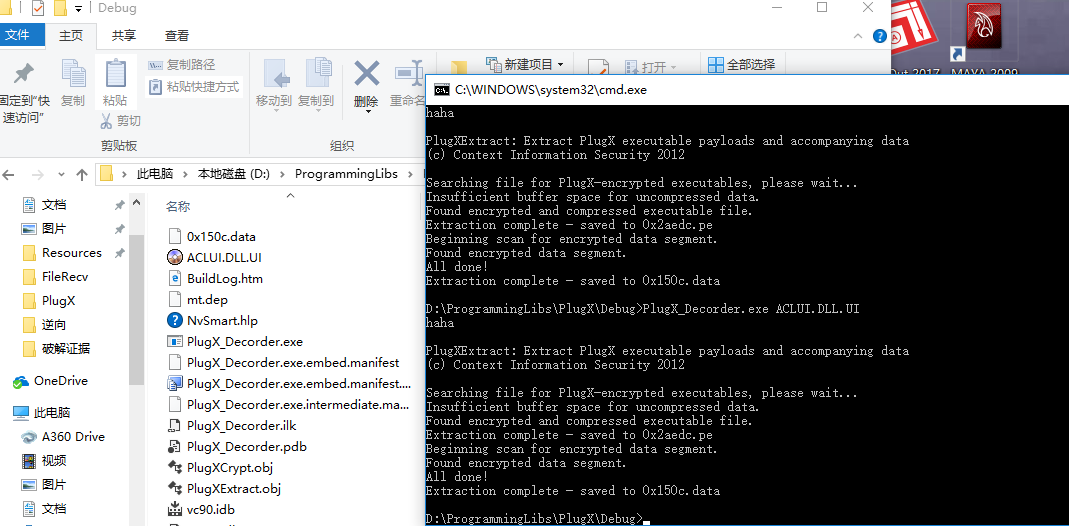
run the tool we got .data file. use winhex to check it
利用winhex查看生成的.data文件
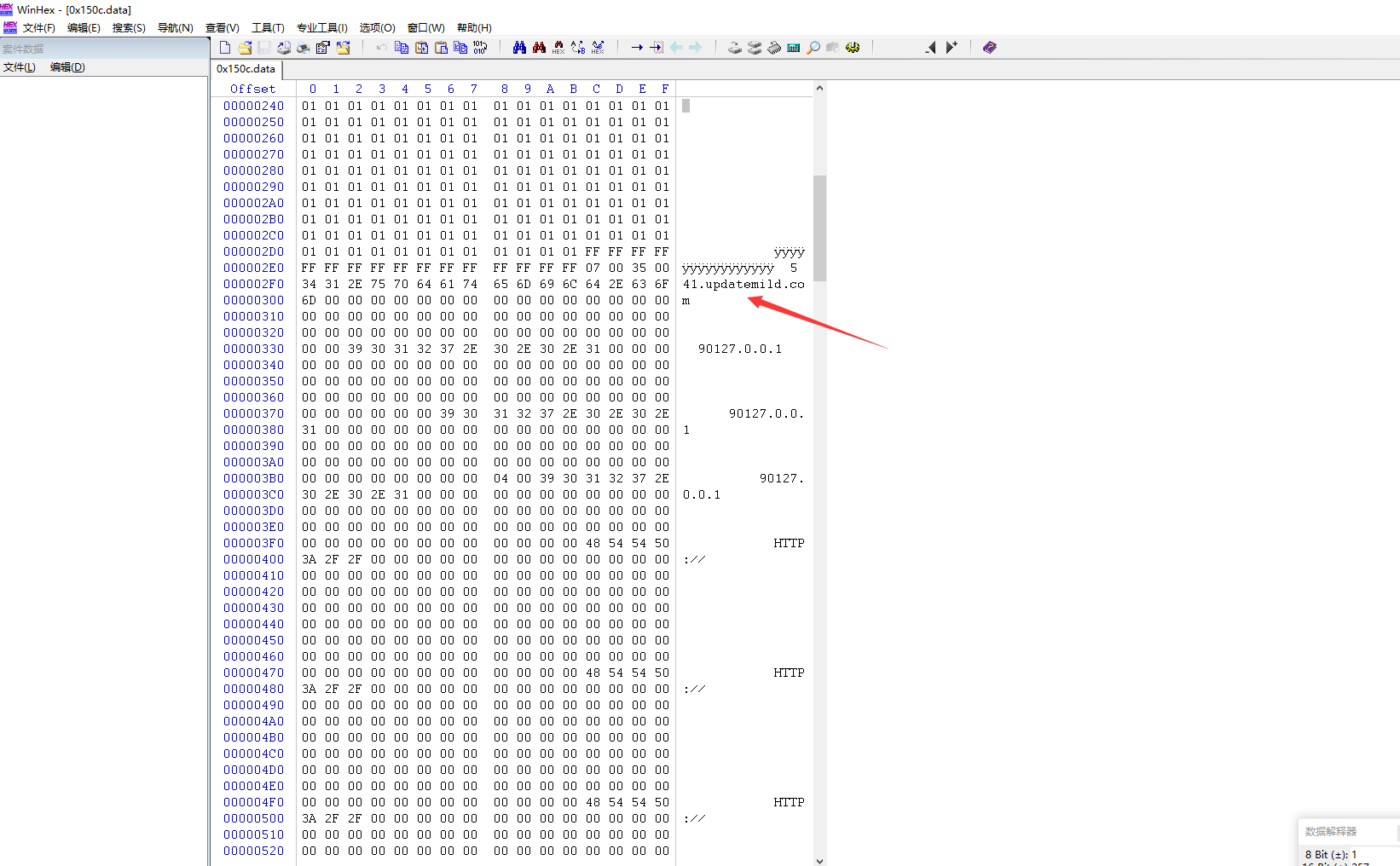
hacker's server used to send command to backdoor program, used to collect information.
黑客服务器域名用于控制操作木马收集肉鸡 信息。

installation path/安装路径
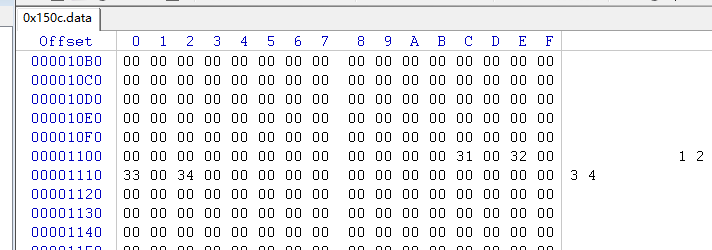
password may used to connect to hacker server./可能是用于认证登陆连接黑客服务器的密码。